About Us
Welcome to ITPS - IT Professional Services LLC
Who are we:
ITPS, has established itself as a provider of high quality services and technology solutions.
As a privately owned company, our team is actively involved in management as well as in daily operations.
Our company continues to experience growth in the rapidly changing technology industry.
Our professional team is providing quality technology solutions increasing clients’ security, efficiency and productivity.
To further benefit our clients, ITPS works with Cisco Meraki, Microsoft, VMware, Dell and many more.
These leading vendors are the best in technical education and continued support.
Our goal is to meet and exceed organizations’ technology needs and expectations with proven technology solutions.
Our Solutions and Services are:
• Network Security Audits
• Network Architecture and Security
• Servers Build, Consolidation, Conversion, Virtualization
• General and Advanced Networking
• Email migrations, Email Security
• Data Backup and Restore / Disaster Recovery
• All-inclusive Managed IT Services
• Computer / Server / Network Device Monitoring and Maintenance
• Printers configuration
• Per-incident for Networks, Servers, Desktops, Notebooks and Printers
• Projects (Migrations, Adds, Changes, Upgrades, etc.)
Who Are We
IT Professional Services company offering managed services on a proactive basis
Our Mission
To empower our clients through exceptional service
What We Do
Deliver IT Professional Services, while you focus on your business goals
Our NIST Cybersecurity Framework Approach
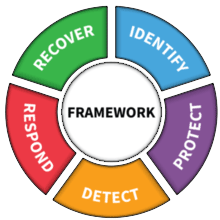
01.
Identify
The Identify Function assists in developing an organizational understanding to managing cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.
02.
Protect
The Protect Function outlines appropriate safeguards to ensure delivery of critical infrastructure services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event.
03.
Detect
The Detect Function defines the appropriate activities to identify the occurrence of a cybersecurity event. The Detect Function enables timely discovery of cybersecurity events.
04.
Respond
The Respond Function includes appropriate activities to take action regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident.
05.
Recover
The Recover Function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident.
Why Choose Us?
- High quality IT support based on the most recent standards and the best IT practices
- We combine results-oriented and project-oriented thinking to make or projects successful
- Collaboration
- Coordination
- Expertise
- Professionalism
- Making the most reliable infrastructure hardware/software choices
- Unifying IT Management
- Expanding Service Portfolio
- Re-evaluating Vendor Selection
- Pursuing Automation
- Never taking the shortcuts
- Always learning
Some Numbers
Over
Years of Experience
More than
Satisfied Clients
Exceeding
Vendors we work with
Beyond
Completed Jobs, and growing
Who we are working with







